Student: Christoph Lagger
Supervisor: Peter Schartner
Unfortunately accidents in alpine environments happen on a daily basis, often during mountain hikes in summer or ski tours in winter. Besides standardized security beacons (e.g. avalanche beep) everybody carries a smartphone with multiple sensors (such as Accelerometers and Gyroscopes among others) with them. In emergency situations, time is crucial and an accurate and robust recognition system in form of a mobile application could trigger the chain of survival automatically and support rescue missions. In this thesis machine learning is used to determine current movement patterns or activities based on sensor data such as walking up/down, skiing down, pause, or in the worst case an emergency situation. We recorded a large dataset of actual movement patterns (7 days, 19 hours, 21 minutes and 22 seconds) from all available smartphone sensors during actual alpine activities. Movement data was analyzed and a comprehensive training dataset was created for further usage. The goal was to determine the best combination of sensors, algorithms, features and window size parameters to accurately detect said movement patterns. A framework was implemented to perform a series of experiments using 10-fold cross validation, evaluate its outcome and visualize movement data as well as simulate results. Evaluation results as well as simulation results showed that the Random Forest algorithm using data from the Gyroscope and Magnetometer sensor in combination with a 4-second sliding window and an overlap of 20%, utilizing the Root Mean Square, Mean, Signal Vector Magnitude, Energy, Variance, and Standard Deviation as features, achieved a promising F-Measure of 0.975.
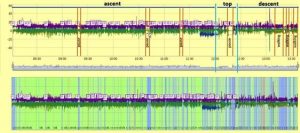
Figure 1: Key activities and corresponding result of a simulation run using the most promising combination of algorithm, sensors, features and sliding window parameters.